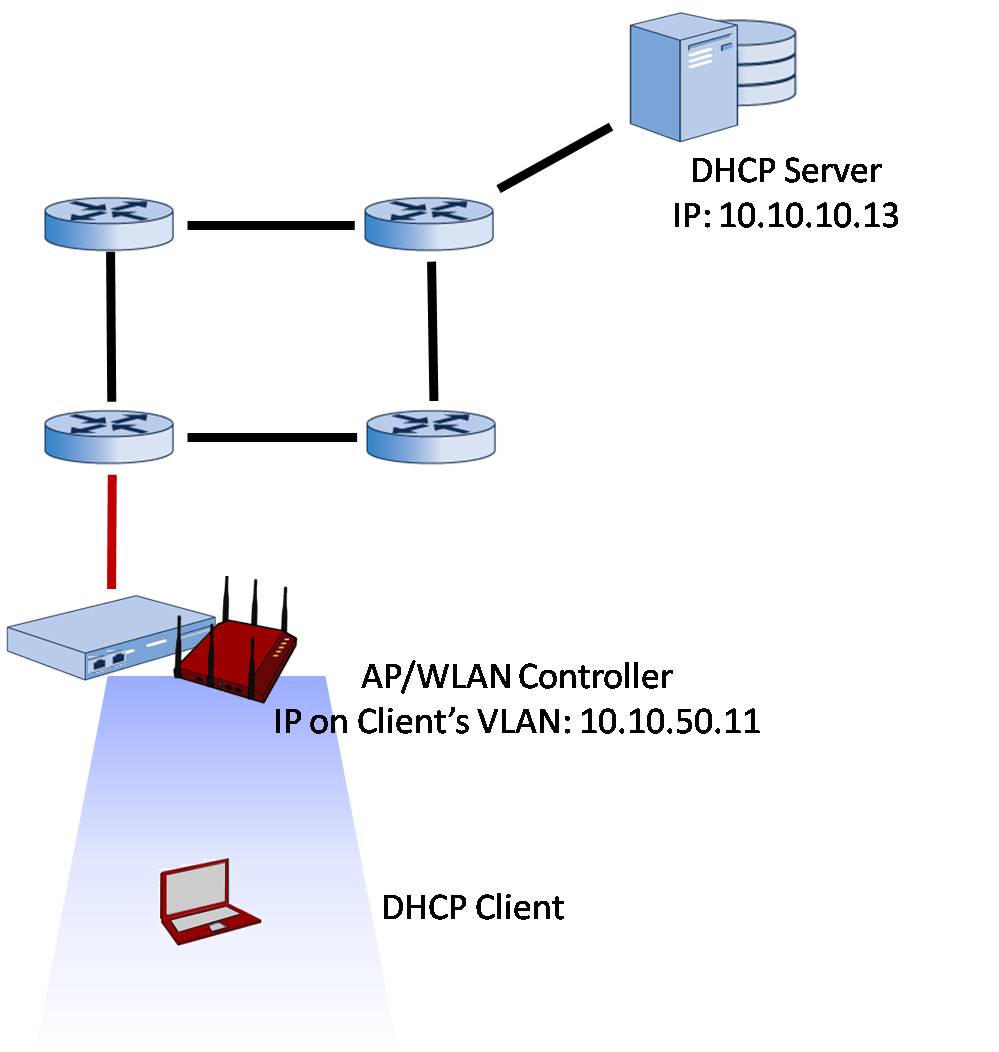
RogueOne: Creating a Rogue Wi-Fi Access Point using a Raspberry Pi | by Bruno Amaro Almeida | Medium
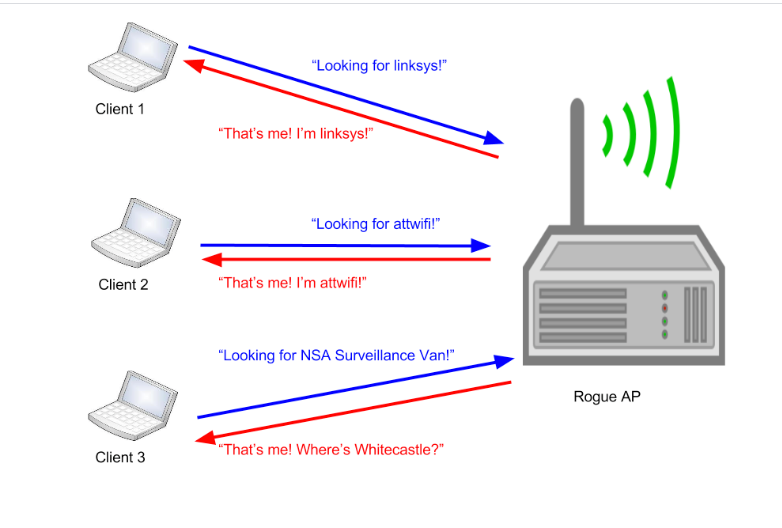
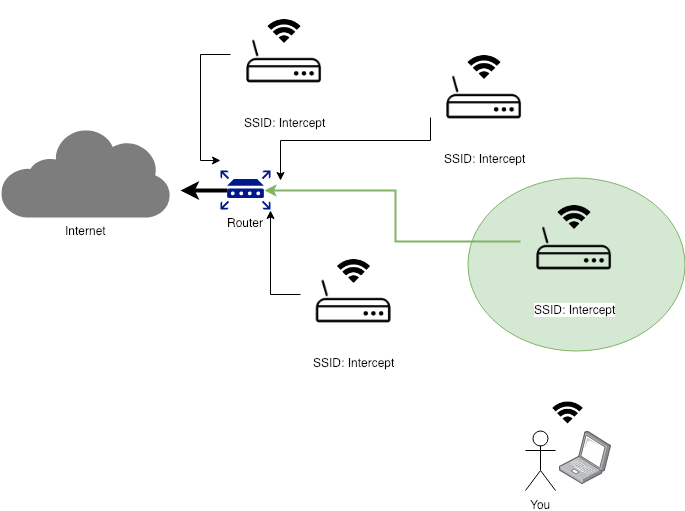
Modern Wireless Tradecraft Pt I — Basic Rogue AP Theory — Evil Twin and Karma Attacks | by Gabriel Ryan | Posts By SpecterOps Team Members
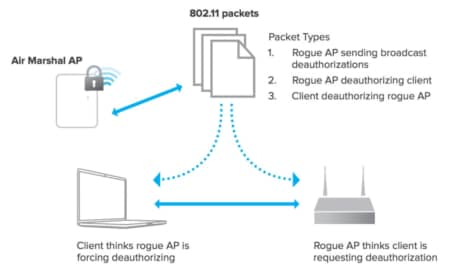


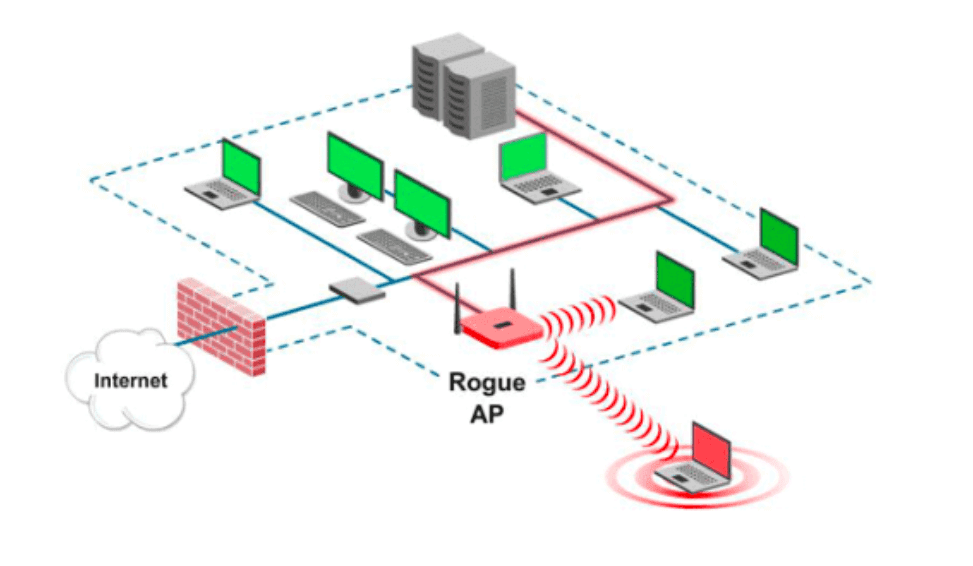
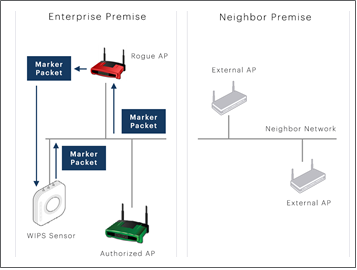


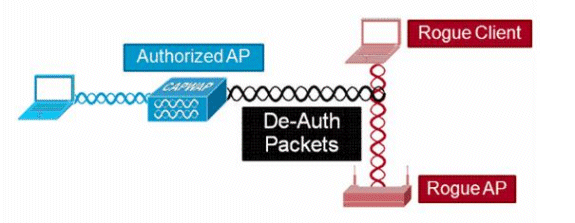
![PDF] Rogue Access Point Detection System in Wireless LAN | Semantic Scholar PDF] Rogue Access Point Detection System in Wireless LAN | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/41a44df312f08ce3551a932335310d6e542e2fa7/4-Figure6-1.png)



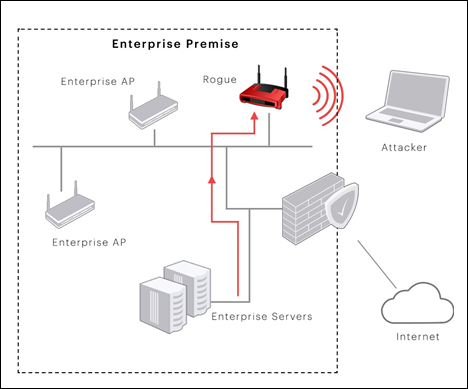


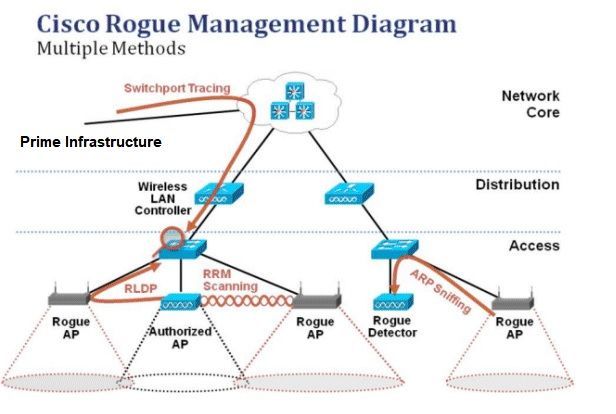
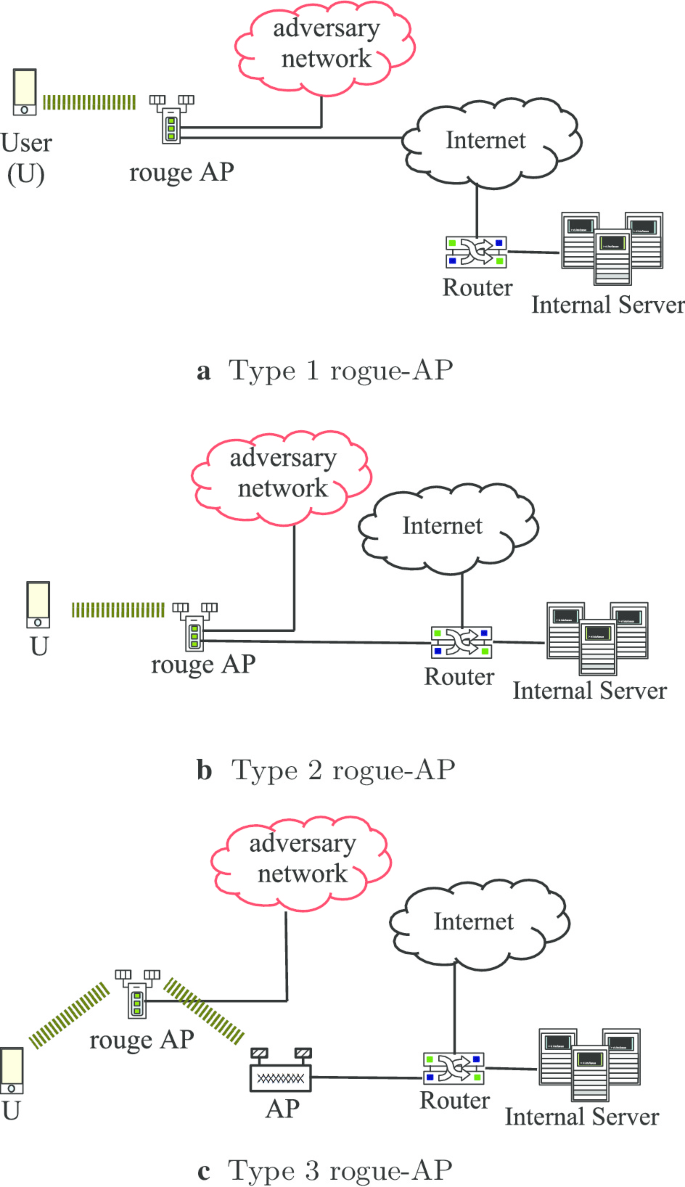
![PDF] A Review of Online Rogue Access Point Detection | Semantic Scholar PDF] A Review of Online Rogue Access Point Detection | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/d0ed1b76a7acad87e8bb816c84444e4cf6a64b7c/2-Figure1-1.png)